You might have noticed the increase in the cases of hacking these recent years, and probably also wonder why it is being referred to as a scam. And you are right to wonder, because calling it a scam would be like trivializing and downplaying the meaning behind it.
Hacking ans scamming are two correlating words under the cyberthreats category. Where scamming is more general and goes way beyond the cybersphere, hacking is confined within and limited to the walls of the cyberworld.
So, what exactly is hacking?
Hacking, as we obviously know, is an unknown person bypassing your system and gaining access to your phone, social media and even bank accounts. They do this to collect your personal information and data, and at times you may not even realize it – until it’s too late.
The Economic Times defines hacking as an ‘unauthorized access to, or control over, a computer network security system for illicit purposes.’ This may be done by manipulating a computer network, or spreading a software that will leak private information.

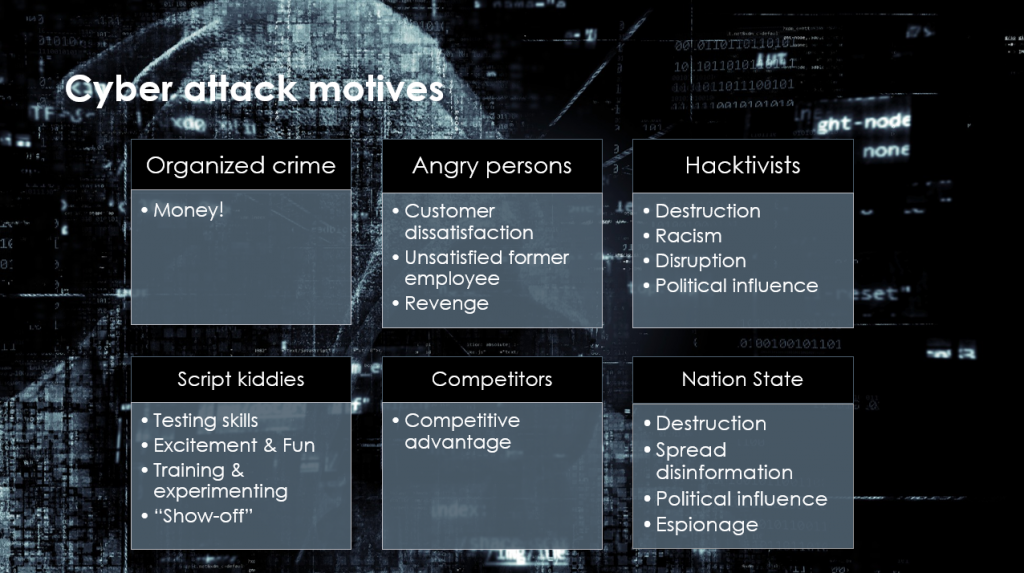
Types of hacking
While we all may be thinking hacking is such a bad thing, some cybersecurity experts do not think so. And this is derived from the three existing three types of hacking.
- White hat hacking – known as ethical hacking and is considered less malicious. It is mainly done to test the network vulnerabilities, and implement stronger security techniques.
- Grey hat hacking – falling between black and white hat hacking, this type of hacking averages the weights of helpful and destructive hacking.
- Black hat hacking – This is the malicious form of hacking in which hackers spread malware to infiltrate into networks and steal personal and/or private information.
Why do hackers hack?
There are a few reasons why people hack:
- Need or want to steal or leak information.
- Want money.
- Want to disrupt services.
- Driven by a selfish motives.
- Have to prove a point.
- To test security vulnerability
- Just for fun.
How does hacking happen?
Hacking happens in the most mundane of ways, and often unexpected. This could be by tricking one into giving up their details by orchestrating scams, also known as phishing. If you receive a random link telling you that you’ve won millions and that you need to provide your bank information in order for them to transfer the money into your account, DO NOT click on the link.
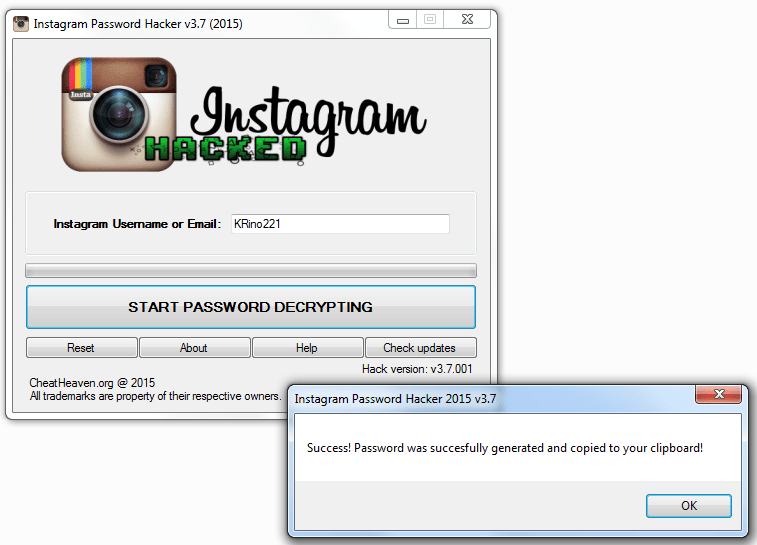
Instagram hacking is considered to be one of the easiest, most common practice of all social media hacking. Many apps available for both Android and iOS users can be used to track and give access to other people’s log in details.
Other methods may be Malware-Injecting Devices. This is when cybercriminals sneak a malware into a USB or other hardware. Once you plug it into your device, you’ve indirectly given access.
Another is Cracking passwords. While some hackers may use password cracking tools, others could just guess what you’d most likely have as a password, which is probably why using your birthday as a password is not a smart idea.
How to avoid being hacked?
- Although it occurs without any warning, it’s still advisable to never share your passwords or important and personal information online.
- Always use strong passwords. This can be done through a combination of random letters, characters and numbers which cannot be easily generated by cracking tools.
- Be careful with online friends and strangers. Even if you know them well enough, you never truly know what they’re doing with the information you give them. Ergo, never give out too much of yourself.
- Avoid clicking on just any link that pops up into your DMs, emails, or WhatsApp messages.
More tricks on how to avoid becoming a victim to hacking can be accessed from here. (And yes, it’s safe to click that link.)

There is more to hacking than meets the eye. And for aspiring white hat hackers, there are many learning resources available for free online where you can master the art of hacking. Better yet, there are institutions that offer qualifications in ethical hacking. The Computer Science path is always an option to consider. And for the kasi hackers, well, go to YouTube.


One Reply to “Hacking – The New Scam On The Block”